This article is the second part to the November 2006 article “Mediating effects of Privacy & Preferences Management on Trust and Consumer Participation in SMS Based Mobile Marketing Initiatives: Part one of Two”).
Part one of this article presents the hypothesis that a firm’s privacy and preferences management program could positively influence consumer trust in a brand and consequently lead to increased consumer loyalty and consumer participation in the firm’s mobile marketing initiatives, which in turn could lead to an increase in consumer consumption of the firms goods and services. In addition, part one analyzes two key elements to privacy and preferences management, Notice and Choice. In this article, part two, the final two key elements of privacy and preference management are discussed, Value and Access & Control. In addition, a conceptual model is presented which visually represents the interaction between privacy and preferences management, trust, and consumer participation in mobile marketing initiatives. Marketers may use the concepts presented here to increase the long-term effectiveness of their mobile marketing initiatives and the relationship they have with their audience.
Mobile marketing is a new and exciting channel that can be added to a marketers marketing mix relatively easily. When properly executed, mobile enhances traditional media. Marketers can inform, entertain, engage, and sell to their audience with pure mobile marketing programs.. However, it is important to note that the mobile channel is unlike any other medium. Mobile marketing is personal (Ideas & Strategies 2001; Barnes & Scornavacca 2004; Karnell 2005; Swiley 2006; Koskinen et al. 2006), interactive (Ideas & Strategies 2001’ Buckley, 2003), and time (Ideas & Strategies 2001; Barnes & Scornavacca 2004; Buckely, 2003) and location independent (Barnes & Scornavacca 2004). The personal nature of the mobile phone is singularly important to individual subscribers and should be to marketers as well, as was pointed out and substantiated by the most recent Mobile Marketing Association (MMA) 2006 Mobile Attitudes and Usage Study. The MMA study found that across all age groups, the mobile phone has become an important part of our everyday lifestyle with many respondents stating that they have become dependent on their mobile device(s). In fact, the study found that 82% of the total sample reported that their mobile phone is high to moderately important to their daily life, and 79% say that they are high to moderately dependent on their mobile phone (MMA 2006). The personal ties between the consumer and the mobile phone are only going to increase, and with this marketers must take special measures to protect the consumer’s personal space and privacy (Roussos et al. 2003; Byron 2006; Karnell 2005; Chowdhury et al. 2006).
As discussed in part 1 of this article, employing Notice and providing Choice are two critical elements to privacy and preferences management, and in fact, are required elements of the industry’s best practices guidelines. Notice refers to the fact that marketers must conspicuously inform consumers as to exactly how their personally identifiable information (PII) and non-personally identifiable information (Non-PII) are going to be used and stored, and Choice refers to the mechanics marketers give consumers to easily opt-in and participate in or easily opt out of any marketing initiative (see part 1 for details). The final two key elements of privacy and preferences management are Value and Access & Control.
Value
The idea of value is fairly simple. Markets need to recognize that a consumer should be rewarded for the sharing of their PII and non-PII with the marketer. As pointed out by Deighton (2004) consumer PII and Non-PII is a tangible asset and consumers should be given value for sharing this with firms. “Unless your offer is compelling and contains an incentive or reward, people will opt-out in droves and your brand will be tarnished” (Air2Web, 2003). Typical forms of value include the personalization of services, the offering of contextually sensitive services, the offering of coupons, free minutes, free and or discounted binary content, monetary incentives, and more. Hanley et. al, (2005) found that in a mobile marketing study of college students that “students are becoming more receptive to cell phone ads, but are not ready to give up their wireless privacy, unless of course they are rewarded, but the reward model seems to be changing.” Hanley (2005) found that nearly 29% of the surveyed students would accept mobile advertising if they received something free (ringtone, wallpaper, game, free minutes, free access to the mobile internet, etc.) or monetary compensation. In 2005 28% would accept a quarter per ad, 35% wanted a $1.00 per ad, and one-fourth wanted more than $1.00 per ad. In 2006, in a follow-on effort to Hanley’s original study, Hanley found that 33% of the surveyed students reported that they would not accept ads at any price, up from 1% in 2005; however, 32% would accept ads for $1.00, 12% for 50 cents, and 25% for 25 cents or lower (Hanley et. al. 2005). Note, one challenge many mobile marketing studies face is the fact that the definition of mobile marketing, when used to introduce the concept of mobile marketing to consumers, is often unclear and tends to focus on push and wireless advertising and not all the other elements that make up mobile marketing. The lack of a clear, concise, and well-founded definition of mobile marketing could be a significant contributor to the apparent low consumer acceptance rates of the concept of mobile marketing or wireless advertising in many studies.
Access & Control
The final consumer-facing element of the privacy and preferences management program is Access & Control. Hann et al. (2005) found that users have a higher regard for web sites that give the ability to access and adjust their personal information. In simple terms, the idea of access is to give consumers access and control over their PII and Non-PII so that they can 1) know what information is being collected, 2) correct any errors in the information, or 3) revoke access to parts or all of the information. Providing access is a simple idea; however, as Loyle (2006) notes, it is not an easy one to execute. Loyle (2006) raises a number of important questions when it comes to offering access to information gathered by an organization:
- What data should be accessible?
- Who should have the right to access it and how are these rules determined to authenticate the man or machine accessing the data?
- What can be done with it?
- What constitutes public vs. private data? What one person considers private another does not care about, how do you distinguish between the two?
- What happens when this information is mixed, i.e. PII, with Non-PII, with 3rd party data?
- What are the liabilities of breaches to access to the data? Who cares?
An additional, and important point, also relates to ownership of the information. Today, as Deighton (2002) points out, all PII and Non-PII are owned by the collector of the information, leaving consumers little rights or control over how information about them is used and disseminated. While, as noted above, the idea of access and control on the web is maturing, it has not come very far with mobile marketing and is very limited. The industry can benefit greatly from work on this area within privacy and preferences management models.
A Conceptual Model
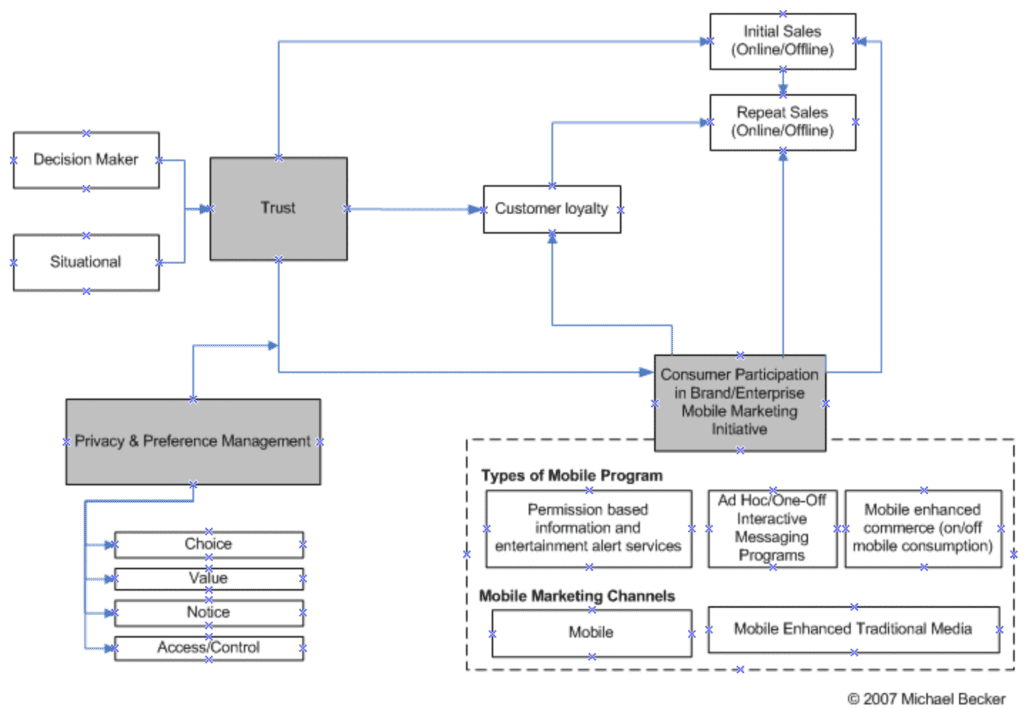
Studies have shown that marketing, and in particular mobile marketing, can be a very effective tool of generating high-response rates to marketing initiatives, sales, brand awareness, and customer loyalty (Kavassalis et al. 2003; Bauer et al. 2005; Rettie et al.; Enpocket 2005;l Leppäniemi et al. 2006). And, as was alluded to above, when consumer’s have trust in a brand and/or marketer they are more inclined to engage in the marketer’s program(s) and share more of their PII to enrich the experience of the interaction (future articles will explore the elements of trust in more detail, but at a minimum it should be understood that trust is both bounded by variables surrounding the one offering the trust, the Decision Maker or trustee, as well as situational factors at the time the trust is being extended, e.g. who is being trusted). The following illustration shows the interactions between these constructs and many of the subordinate variables that support them.
To this author’s knowledge, the above conceptual model represents the first time it has been proposed that privacy & preference management may have a mediating effect on consumer trust and consumer participation in marketing initiatives. While this article puts forth the proposal that this effect exists, research needs to be performed to validate and quantify the level of any such effect.
Conclusion
This paper may be used as a foundation for future research into the relationships between trust, privacy and preferences management, and the consumer acceptance and participation in mobile marketing initiatives. It is important for marketers to recognize that a relationship with a customer is not a static event, but an on-going process. Mobile marketing, when properly used, can be an effective tool within the marketer’s arsenal to nurture this relationship. Through mobile marketing practices marketers can entertain, inform, build brand awareness, create loyalty, and drive purchase decisions amongst their target consumers; however, to ensure continued success and long term longevity of mobile marketing as a viable medium consumer trust must be established and maintained.
Notice to readers:
This two part article is a brief summary of some of the issues of privacy and mobile marketing and is based on a larger work conducted by this author into the effects of privacy and preferences management on trust and consumer participation in mobile marketing. Readers that are interested in this topic and the expanded work by this author are encouraged to contact the author at research@mmaglobal.com and share their thoughts and ideas.
References
Air2Web (2003). Permission Based Mobile Marketing. Atlanta.
Barnes, S. J., & Scornavacca, E. (2004). Mobile marketing: The role of permission and acceptance. Int. J. Mobile Communication, 2(2), 128~139.
Bauer, H., Barnes, S., Reichardt, T., & Neumann, M. (2005). Driving Consumer Acceptance of Mobile Marketing: A Theoretical Framework and Empirical Study. Journal of Electronic Commerce & Research, 6(3).
Buckley, Russell. (2003, 3/25). Mobile Marketing - R U up 4 It? MarketingProfs.com. Retrieved 11/10/03, from http://www.marketingprofs.com/3/buckley1.asp.
Byron, E. (2006, 10/July). And Now a Word From.. The Wall Street Journal (New York), sec. THE JOURNAL REPORT: LEADERSHIP, p. a.
Chowdhury, H., Parvin, N., Weitenberner, C., & Becker, M. (2006, December). Consumer Attitude Toward Mobile Advertising in an Emerging Market: An Empirical Study. International Journal of Mobile Marketing, 1(2).
Deighton, J. (2002, 26/May). Market Solutions to Privacy Problems?, Harvard Business School, Boston, MA.
Deighton, J., & Schindler, R. (2004, 12/May). The Presentation of Self in the Information Age. (. Harvard Business School.
Enpocket Mobile Media Monitor US reveals young adults value mobile more than traditional media.
(2005, 21st July). Retrieved from Enpocket: http://www.enpocket.com/wrapper/page/news/2005/july21.html.
Hanley, M., Becker, M., & Martinsen, J. (2006, June). Factors Influencing Mobile Advertising Acceptance: Will Incentives Motivate College Students to Accept Mobile Advertisements? International Journal of Mobile Marketing, 1(1), 50~58.Hanley, M., Martinsen, J., & Pryor, L. (2005, November). College Cell Phone Advertising Survey., Department of Journalism, Ball State University.
Ideas & Strategies for Implementing Mobile Marketing. SkyGo. (2001).
Information Age. (2006). Retrieved 12/15/06, from Answers.com: http://www.answers.com/topic/information-age.
Karnell, J. (2005, 14/February). Mobile marketing primer. Retrieved from http://www.onetooneinteractive.com/resource/whitepapers/0010.html.
Kavassalis, P., Spyropoulou, N., Drossos, D., Mitrokostas, E., G., Gregory, & Hatzistamatiou, A. (2003, Fall). Mobile Permission Marketing: Framing the Market Inquiry. International Journal of Electronic Commerce, 8(1), 55-79.
Koskinen, I., Repo, P., & Hyvonen, K. (2006, November). Journal of Usability Studies, 2(1), 22~38.
Leppäniemi, M., Sinisalo, J., & Karjaluoto, H. (2006, June). A Review of Mobile Marketing Research. International Journal of Mobile Marketing, 1(1), 30~42.
Loyle, D. (2006, 9/August). Privacy Under Scrutiny. Retrieved 8/9/2006, from http://www.targetonline.com.
Rettie, R., Grandcolas, U., & Deakins, B. Text Message Advertising:Dramatic Effect on Purchase Intension., Kingston University & BT.
Roussos, G., Peterson, D., & Patel, U. (2003, Fall). Mobiel Identity Management: An Enacted View. International Journal of Electronic Commerce, 8(12), 81-100.
Swilley, Esther & Hofacker, Charles (2006, December). Defining Mobile Commerce in a Marketing Context. International Journal of Mobile Marketing, 1(2). 18~23.

No Comments.