What's one of the biggest things on the peripheral of tech that is (should be) capturing people's attention so that they can prepare for the future? For me, the answer is
Decentralized identity is going to reshape industry and society as we know it since it has the potential to reshape the Internet. Decentralized identity will empower individuals to take control of how their personal data, their identity, and attributes of their identity, are shared and exchanged through the Internet.
Decentralized identity will give individuals, rather than private and public institutions, control of their identity and personal information.
Decentralized identity is coming. Mastercard, among other industry leaders (e.g. Microsoft, SAP, Adobe, IBM) see the importance of decentralized identity and giving people more control over their identity and personal data. December '18 Mastercard and Microsoft announced a decentralized universal ID partnership. March '19 Microsoft, SAP, and Adobe announced the formation of the Open Data Initiative and Mastercard released a whitepaper built around decentralized identity "Restoring Trust in a Digital World."
It will take years for decentralized identity, and a new Internet, to fully emerge. It is important to monitor the decentralized identity trends and prepare for the future, but it is equally important to provide solutions today that provide immediate value to the individuals we serve.
Understanding the Three Identity Authentication Methods: Centralized, Federated, and Decentralized
There are three methods for managing identity, and eventually, personal data: centralized identity, federated identity, and decentralized identity.
Centralized Identity & Federated Identity Management
Today, individuals, when online, have their identity verified through one of two methods, centralized identity authentication or federated identity authentication methods.
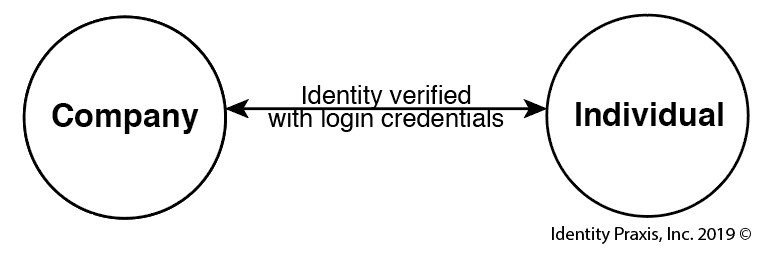
In the centralized identity authentication model (Figure A) individuals authenticate their identity directly with a company’s sites, typically with a username and password (aka with credentials) and increasingly with some form of multi-factor authentication (MFA), that is when sites offer MFA as an extra layer of security to double check the verification of an individual's identity.
In a federated identification authentication model (Figure B) an individual authenticates their identity when attempting to log in to a company's site by using credentials from a second company that the first company trusts, a federated ID provider, such as Google, Facebook, Twitter, or another single sign-on service provider.
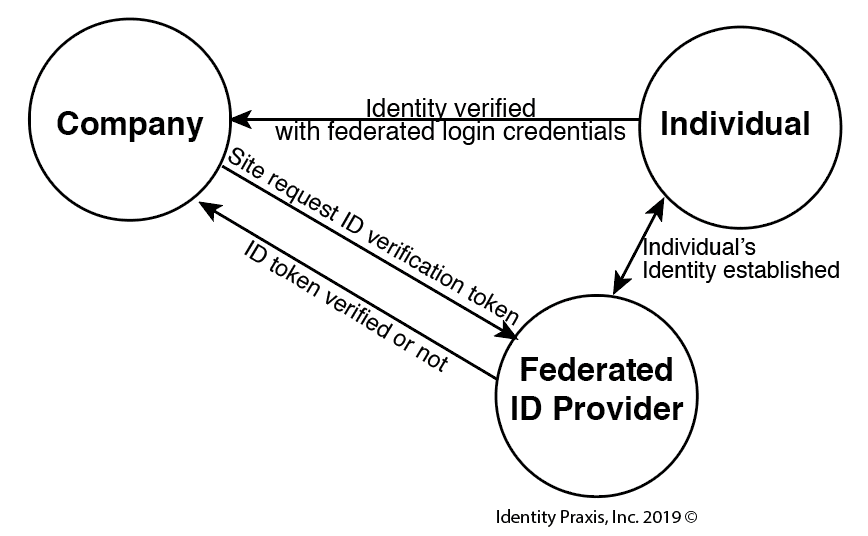
Both the centralized and federated authentication models have their pros and cons when it comes to value, convenience, privacy, and security. The pros are that both models are established and understood by all parties. They provide value. They are convenient, especially when credentials are used across sites, a practice that is not recommended. They work. The cons are that the methods create a single point of privacy and security failure; that is, individuals identity credentials are in a single, or multiple, database(s) that can get hacked, leaked, and personal data can be misused, and the company and federated ID provider potentially know how and where individuals are using their identity and personal data.
Solutions That Provide Immediate Value
Individuals are taking action, adopting new behaviors and technologies, to control and protect their identity and personal information (see MEF Global Consumer Trust Report 2018). On the technology front, people are adopting personal information management solutions (PIMS), cyber-security services, traditional identity & financial services monitoring and protection services. For example people are adopting password managers, ad blockers, identity (email, phone number) aliasing tools, personal data stores, quantified self & personal visualization tools, virus protection, malware & ransomware management software, identity insurance, credit monitoring & reporting services, darknet monitoring services, and more. These services are incredibly important and are an immediate answer to people's desire for identity and personal information management and protection.
Introducing Decentralized Identity Management
Industry innovators believe there is a new identity management method on the horizon, other than centralized or federated identity management, namely decentralized identity.
With decentralized identity, the individual themselves, not a company and not a federated service, is in control of their identity (See Figure C).
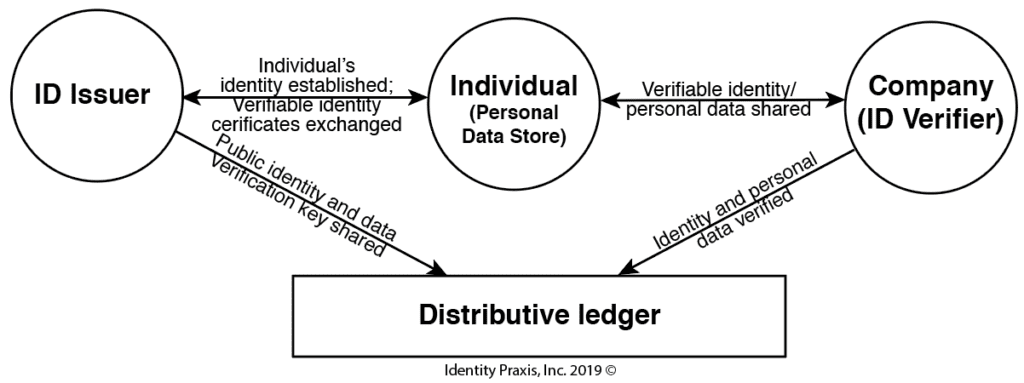
There are a few steps for making decentralized identity work.
First, the individual receives verifiable identification credentials (e.g. passport or drivers license) or veritable certificates (e.g. a diploma) from an ID issuer, like the DMV, a company, a college, etc.
Second, the individual requests and receives a verifiable digital certificate for their verifiable identification or verifiable personal datum certificate by issuing a Decentralized Identifier, a DID, to the ID issuer. The ID issuer provides the verifiable digital certificate to the individual, as well as puts a public non-reputable, verifiable, authenticatable public confirmation record of the individual's identity or datum certificate in a distributive ledger. Distributive ledgers are implemented using blockchain or a similar decentralized cryptographic data processing scheme.
Finally, when an individual wants to use their identity or have any attribute of their identity verified all they need to do is present a company (aka ID verifier) with their verifiable digital certificate. The company will check the distributive ledger to verify the individual's identity or personal data attribute is valid. For example, if an individual wants to go to a bar and needs to prove they're over 21, rather than handing over their drivers license and disclosing too much information they can hand over a verifiable certificate that represents they are over 21. It is a win-win. The bar can verify the individual is over 21 and serve the individual, while the individual gets into the bar while simultaneously protecting their privacy. Note, this process may include the use of text messaging, specialized apps, QR codes, fingerprints, FaceIDs or similar verification capabilities to facilitate the transaction.
The two primary goals of decentralized identity solutions are to decentralize authority over individuals data and ensure verifiability for whoever is wielding control over an individuals data.
With decentralized identity solutions, individuals will only disclose the bare minimum of their personal information needed to perform an action or transaction and will ensure there is no single point of failure that might lead to the misuse of individuals identity and personal data. These solutions are expected to enhance individuals privacy since credential issuers do not need to be told where or when individuals are using their identity and data and ID verifiers do not need to know anything about the issuer. Eventually, these solutions may be used to tokenize data, sign data, so that all data will be controlled by their creator or designated owner.
There is a lot more to this process that can be explained, this is simply a high-level overview; I'll reserve more for future articles.
To learn more about decentralized identity visit the Decentralized identity Foundation (DIF), Sovrin Foundation, or Veres One; that is, example industry communities and leading players shaping the future of decentralized identity. Moreover, for a detailed overview of decentralized identity technical specifications, specifically for DIDs, see the March 2019 W3C Community Group's Decentralized Identifiers (
Next Steps for Decentralized Identity & The New Internet
To bring decentralized identity to life private and public institutions, and Individuals all need to come together and align their goals around concepts like data ownership and digital sovereignty, such as the ability for individuals to maintain autonomy, self-determination, and free will. New technologies need to be created. New specifications, standards, and regulations must be established. New business models need to be formed, tested, and accepted. New cultural norms need to be embraced. And, many political debates need to be had and consensuses need to prevail. All of which are in the works.
It is going to take years for decentralized identity models to fully mature and be adopted by individuals, public and private institutions. Eventually, decentralized identity will make its way into identity, PIMS, and cyber-security offerings; moreover, new solutions will emerge. For now, to be able to develop it and eventually use it responsibly, it is essential that we discuss the potential of decentralized identity. We need
Stay tuned. In the not too distant feature, a new Internet is going to emerge. This new Internet will fundamentally influence individuals attitudes and behaviors, experience, and expectations, change the nature of physical products and services, and business models. It will give rise to the personal information economy, an economy where individuals are in control of and have the ability to conveniently participate in the value exchange of their identity and personal information

No Comments.