Art- A call for New Industry Data Exchange Models, The Trust Chain, and A Connected Individual Transaction And Identity Scoring Scheme: An Interview with Virginie Debris of GMS
I recently sat down with Virginie Debris, the Chief Product Officer for Global Messaging Service (GMS) and Board Member of the Mobile Ecosystem Forum, to talk about personal data and identity (PD&I). We had an enlightening discussion (see video of the interview: 46:16 min)). The conversation took us down unexpected paths and brought several insights and recommendations to light.
In our interview, we discussed the role of personal data and identity and how enterprises use it to know and serve their customers and protect the enterprises’ interests. To my delight, we uncovered three ideas that could help us all better protect PD&I and improve the market’s efficiency.
- Idea One: Build out and refine “The Trust Chain”, or “chain of trust,” a PD&I industry value chain framework envisioned by Virginie.
- Idea Two: Refine PD&I industry practices, optimize all of the data that mobile operators are holding on to, and ensure that appropriate technical, legal, and ethical exchange mechanisms are in place to ensure responsible use of PD&I.
- Idea Three: Standardize a connected individual identity scoring scheme, i.e., a scheme for identity and transaction verification, often centralized around mobile data. This scheme is analogous to credit scoring for lending and fraud detection for credit card purchases. It would help enterprises simultaneously better serve their customers, protect PD&I, mitigate fraud, and improve their regulatory compliance efforts.
According to Virginie, a commercial imperative for an enterprise is knowing their customer–verifying the customer’s identity prior to and during engagements. Knowing the customer helps enterprises not only better serve the customer, but also manage costs, reduce waste, mitigate fraud, and stay on the right side of the law and regulations. Virginie remarked that her customers often say, “I want to know who is my end user. Who am I talking to? Am I speaking to the right person in front of me?” This is hard enough in the physical realm, and in the digital realm it is even more difficult. The ideas discussed in this interview can help enterprises answer these questions.
Consumer Identity and the Enterprise
The mobile phone has become a cornerstone for digital identity management and commerce. In fact, Cameron D’Ambrosi, Managing Director of Liminal, has gone as far as to suggest mobile has an irreplaceable role in the digital identity ecosystem.1 Mobile can help enterprises be certain whom they are dealing with, and with this certainty help them, with confidence, successfully connect, communicate, and engage people in nearly any transactions.
To successfully leverage mobile as a tool for customer identity management, which is an enabler of what is known as “know your customer” or KYC, enterprises work with organizations like GMS to integrate mobile identity verification into their commercial workflow. In our interview, Virginie notes that GMS is a global messaging aggregator, the “man in the middle.” It provides messaging and related services powered by personal data and identity to enterprises and mobile operators, including KYC services.
Benefits gained from knowing your customer
There is a wide range of use cases for why an enterprise may want to use services provided by players like GMS. They can:
- Improve customer experience: Knowing the customer and the context of a transaction can help improve the customer experience.
- Maintain data hygiene: Ensuring data in a CRM or customer system of record that is accurate can improve marketing, save money, reduce fraud, and more.
- Effectively manage data: Reducing duplicate records, tagging data, and more can reduce costs, create efficiency, and generate new business opportunities (side note: poor data management costs enterprises billions annually).2
- Ensure regulatory compliance: Industry and government best practices, legislation, and regulation is not just nice to have; it is a business requirement. Staying compliant can mitigate risk, build trust, and help organizations differentiate themselves in the market.
- Mitigate cybercrime: Cybercrime is costing industry trillions of dollars a year (Morgan (2020) predicts the tally could be as much as $10.5 trillion annually by 2025).3These losses can be reduced with an effective strategy.
The connected individual identity scoring scheme
When a consumer signs up for or buys a product or service, an enterprise may prompt them to provide a mobile number and other personal data as part of the maintenance of their profile and to support the transaction. An enterprise working with GSM, in real-time, can ping GMS’s network to verify if the consumer-provided mobile number is real, i.e., operational. Moreover, they can ask GMS to predict, with varying levels of accuracy, if a mobile number and PD&I being used in a transaction is associated with a real person. They can also ask if the presumed person conducting the transaction can be trusted or if they might be a fraudster looking to cheat the business. This is a decision based on relevant personal information provided by the individual prior to or during the transaction, as well as data drawn from other sources.
This type of real-time identity and trust verification is made possible by a process Virginie refers to as “scoring.” I refer to it as “the connected individual identity scoring scheme.” Scoring is an intricate and complex choreography of data management and analysis, executed by GMS in milliseconds. This dance consists of pulling together and analyzing a myriad of personal data, deterministic and probabilistic identifiers, and mobile phone signals. The actors in this dance include GMS, the enterprise, the consumer, and GMS’s strategic network of mobile network operators and PD&I aggregator partners.
When asked by an enterprise to produce a score, GMS, in real-time, combines and analyzes enterprise-provided data (e.g., customer name, addresses, phone number, presumed location, etc.), mobile operator signal data (e.g., the actual location of a phone, SIM card, and number forwarding status), and PD&I aggregator supplied data. From this information, it produces a score. This score is used to determine the likelihood a transaction being initiated by “someone” is legitimate and can be trusted, or not. A perfect score of 1 would suggest that, with one hundred percent certainty, the person is who they say they are and can be trusted, and a score of zero would suggest they are most certainly a cybercriminal.
In our interview, Virginie notes, “nothing is perfect, we need to admit that,” thus suggesting that one should never expect a perfect score. The more certain a business wants to be, i.e. the higher score they require to confirm a transaction, the more the business should expect the possibility of increased transactional costs, time, and friction in the user experience. Keeping this in mind, businesses should develop a risk tolerance matrix, based on the context of a transaction, to determine if they want to accept the current transaction or not. For example, for lower risk or lower cost transactions (e.g., an online pizza order) the business might have a lower assurance tolerance and will accept a lower score. For higher-risk or higher-cost transactions (e.g., a bank wire transfer), they might need a higher assurance tolerance and accept only higher scores.
Example: Detecting fraud in a banking experience
Virginie used a bank transaction as an example. She explained that a bank could check if a customer’s mobile phone is near the expected location of a transaction. If it was not, this might suggest there is a possibility of fraud occurring, which would negatively impact the score.
Mobile scoring happens every day, but not always by this name–others refer to it as mobile signaling or mobile device intelligence. However, Virginie alluded to a challenge. There is no industry standard for scoring, which may lead to inconsistencies in execution and bias across the industry. She suggested that more industry collaboration is needed to prevent this.
The Trust Chain
During our conversation, Virginie proposed a novel idea which frames what we in the industry could do to optimize the PD&I value and use it responsibly. Virginie said we need to build a chain of trust amongst the PD&I actors, “The Trust Chain”.
I have taken poetic license, based on our conversation, and have illustrated The Trust Chain in the figure below. The figure depicts connected individuals* at the center, resting on a bed of industry players linked to enterprises. A yellow band circles them all to illustrate the flow of personal data and identity throughout the chain.

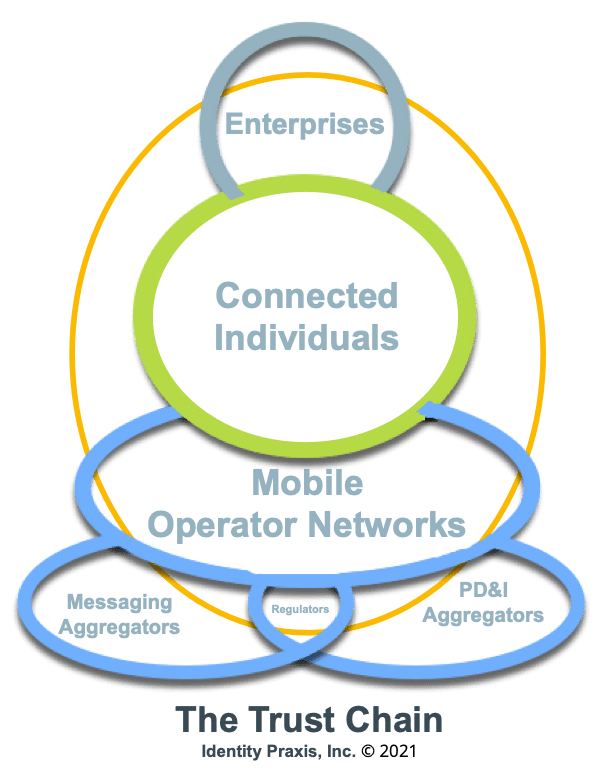
- Defining the connected individual and being phygital: It is so easy in business to get distracted by our labels. It is important to remember the terms we use to refer to the people we serve—prospect, consumer, patient, shopper, investor, user, etc.—are contrived and can distract. These terms are all referring to the same thing: a human, an individual, and more importantly, a contextual state or action at some point along the customer journey, i.e., sometimes I am a shopper considering a product, other times I am a consumer using the product. The shopper and the consumer are not always the same person. Understanding this is important to ensure effective engagement in the connected age. In the context of today’s world and this discussion, the individual is connected. They are connected with phones, tablets, smartwatches, cars, and more. These connections have made us “phygital” beings, merging the digital and physical self. Each and every one of these connections is producing data.
According to Virginie, the key to making the industry more effective and efficient is to tap into more and more of the connected individual data held and managed by mobile network operators. This is because, in her own words, “they know everything.” To tap into this data, Virginie said a number of technical, legal, and ethical complexities must be overcome. In addition, an improved model for data exchange amongst the primary actors of the industry—mobile network operators, enterprises, messaging aggregators (like GMS), and PD&I aggregators—needs to be established. In other words, “The Trust Chain” needs to be refined and built. The presumption behind all of this is that the current models of data exchange can be found wanting.
What we need to do next
In summary, the conclusion I draw from my interview with Virginie are that we should come together to tackle:
- The technical, legal, and ethical complexities to enable more effective access to the treasure trove of data held by the mobile network operators
- The standardization of a connected individual scoring scheme
- The development and integrity for “The Trust Chain”
My takeaway from our discussion is simple, I agree with her ideas. These efforts and more are needed. The use of personal data and identity throughout the industry is accelerating at an exponential rate. To ensure all parties can safely engage, transact, and thrive, it is critical that industry leaders develop a sustainable and responsible, marketplace.
I encourage you to watch to the full interview here.

No Comments.