I've been spending a lot of time thinking about and drilling into the nature of personal information. I've been thinking about its role within society, and how we can find a risk-reward equilibrium (i.e., The Identity Nexus®) when it comes to the exchange of personal information between public institutions, private organizations, and people (i.e., data subjects).
To make this exercise manageable, I landed on three critical cornerstones that we should all consider to equitably manage and exchange personal information, namely privacy, security, and compliance.
Personal Information Management Cornerstones
The three cornerstones of personal information management are,
- Privacy, the ability for a data subject to have agency over their phygital self, that is the ability to control the who, what, when, where, for how long, and for what purpose any entity can access and use their physical or digital self (aka personal information), or capital assets (i.e. the physical asset or any data produced by those assets, such as a connected car, house, clothes, phone, pet, etc.)
- Security, the technologies and processes that ensure only authorized people, systems or services, etc. can access an individual's physical and digital self or capital assets.
- Compliance, the rules, the policies, the rights, and governance models that we all technologically and socially agree to follow when it comes to personal information management (e.g. collection, storage, aggregation, refinement, dissemination, exchange, valuation, etc.), and the punishment if any of these rules, policies, rights, and governance models are not followed or are breached.
I'll write more on each of these cornerstones later, but I wanted to take a moment to talk about compliance briefly.
Personal Information Management Compliance
Without effective personal information management compliance, there will be little chance of achieving The Identity Nexus. People and their data will be "legally" abused (more than they are now), criminals will run amuck, and there will be a total loss of trust. We'll be facing chaos, anarchy.
Regulations are an important and key element of personal information management compliance. Personal information management regulations are the society and industry laws and policies we all agree to and/or are subjected to to give people rights to their data and the guardrails we put on organizations' to ensure that they properly steward people's data.
For those whose job it is to write and manage regulations, wrapping one's head around the nuances of all the personal information management regulations can be quite a challenge, and for the laymen, it can be nearly impossible. Luckily, we have organizations like the Intonational Association of Privacy Professionals that does yeoman's work in helping their members and the industry at large navigate the personal information regulatory landscape.
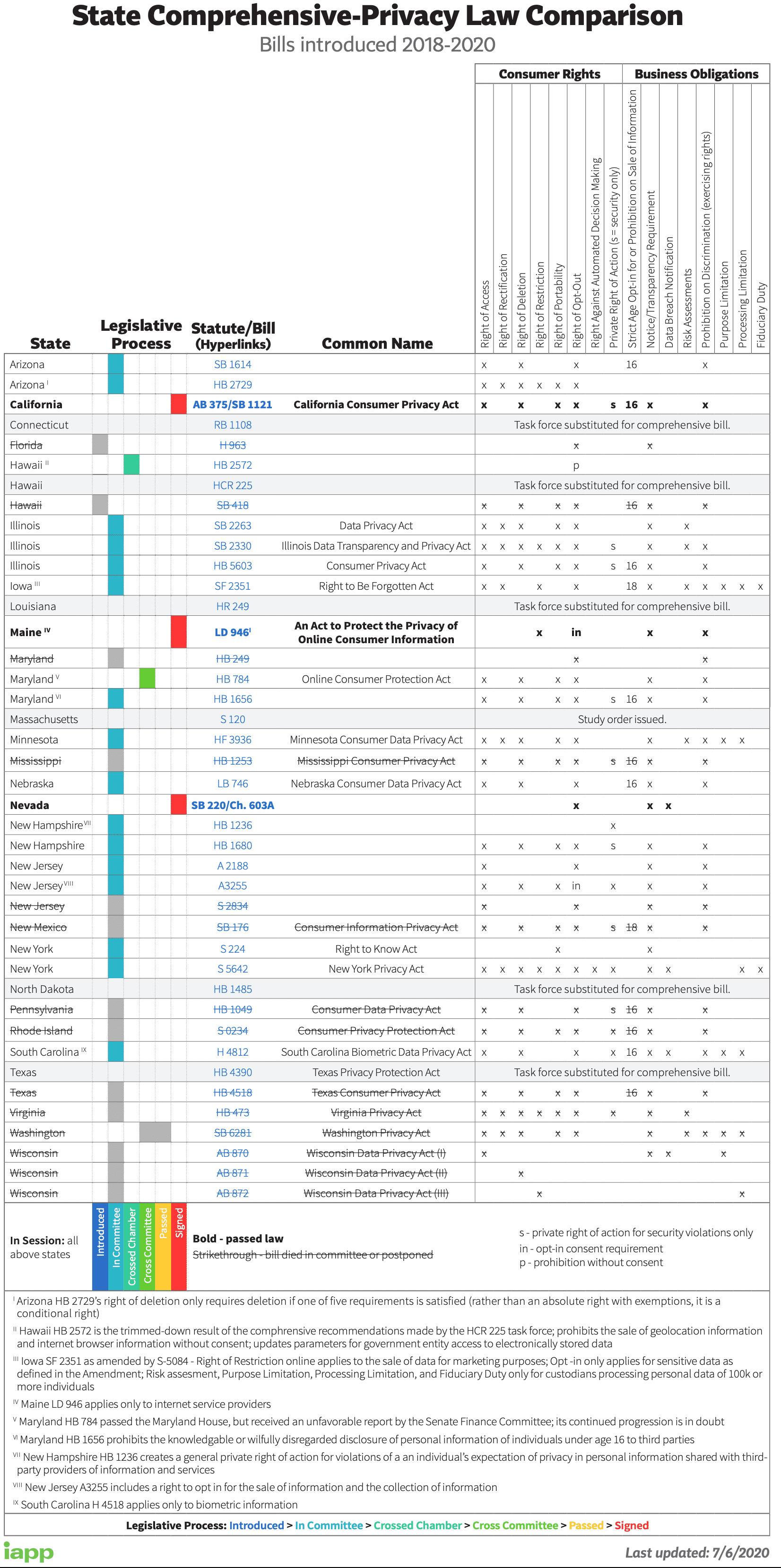
IAPP US State Comprehensive Privacy Law Comparison
On July 7, 2020, the IAPP released an update to its US state comprehensive privacy law comparison, a matrix that evaluates the personal information management regulations in the works across the states. The matrix lists the stage each relevant privacy legislative effort is in within a given state, and the eight most common rights each law affords individuals and the eight obligations that organizations must adhere to (see the image below).
People's personal information management rights
- Right of access
- Right of rectification
- Right of deletion (aka right to be forgotten)
- Right of restrictions
- Right of portability
- Right of opt-out
- Right against automated decision making
- Private right of actions
Organization's obligations toward personal information stewardship
- Strict age opt-in or opt-out or the prohibition on the sale of information
- Notice/transparency requirement
- Data breach notification
- Risk assessments
- Prohibition on discrimination when exercising rights
- Purpose limitations
- Processing limitations
- Fiduciary duty
It is essential for every one of us to study and understand how these laws can benefit us personally and how they may affect our businesses, now and in the future. With this understanding we can then strive to find the equilibrium state for the flows of personal information within society, we can find The Identity Nexus. That is we can ensure that there is an equality of value exchange to risk amongst all those participating throughout the personal information management economy.
The Identity Nexus is a registered trademark of Identity Praxis, inc.

No Comments.